Warning: broken grml96-full_2013.02.iso download
There was a “broken” grml96-full ISO on our mirrors for a few hours. All our checksum files as well as the signature files are OK, just the file grml96-full_2013.02.iso has a few different bits, resulting in a file which doesn’t correspond to the expected checksum. Note: the broken ISO doesn’t do any harm (it even boots) but you should still grab the correct one.
We’ve updated the grml96-full_2013.02.iso file but it might take a few hours until it’s propagated to all our mirrors. To check whether you’re affected execute ‘md5sum -c grml96-full_2013.02.iso.md5’ or ‘sha1sum -c grml96-full_2013.02.iso.sha1’.
The broken file is:
% md5sum grml96-full_2013.02.iso
b2ae41161908751c4ba6ac4db0855a70 grml96-full_2013.02.iso
% sha1sum grml96-full_2013.02.iso
f61a87223ca02482f7f7e8d674c444c40ca91b3a grml96-full_2013.02.iso
The known-to-be-good file should return:
% md5sum grml96-full_2013.02.iso
ceaec04b29f9263e384a54cda8c3bab0 grml96-full_2013.02.iso
% sha1sum grml96-full_2013.02.iso
c95df860f1c08cd7e82ddeac4918bb29cb3f0b7d grml96-full_2013.02.iso
Sorry for the annoyance. Thanks to zeldor for bringing this issue to our attention.
Grml - new stable release 2013.02 available
We just released Grml 2013.02 - Grumpy Grinch.
This release brings the Grml tools towards the upcoming Debian stable release (AKA wheezy), provides up2date hardware support and fixes known bugs from the previous Grml release.
More information is available in the release notes of Grml 2013.02.
Grab the latest Grml ISO(s) and spread the word! Thanks everyone involved and happy grml-ing!
First Release Candidate of Grml version 2013.02 released
We are proud to announce the first release candidate of the upcoming version 2013.02, code-named ‘Grumpy Grinch’!
This release brings the Grml tools towards the upcoming Debian stable release (AKA wheezy), provides up2date hardware support and fixes known bugs from the previous Grml release.
For detailed information about the changes between 2012.05 and 2013.02 have a look at the official release announcement.
Please test the ISOs and everything you usually use and report back, so we can complete the stable release soon. If no major problems come up, the next iteration will be the stable release, which is scheduled for end of February.
New Grml developer: Markus Rekkenbeil
We’re proud to be able to announce that Markus ‘bionix’ Rekkenbeil just joined the Grml team. Welcome in the team, Markus!
Grml - new stable release 2012.05 available
We just released Grml 2012.05 - Ponyhof.
Thanks for all the feedback we received for our 2011.12 release, we took it serious and hope that everyone finds 2012.05 such a wonderful release as we consider it to be.
There were some changes between 2012.05-rc1 and the new stable release. The most important ones are:
- Update to Kernel 3.3.7
- Added sysstat (and imvirt-helper was pulled in as dependency)
- Fixed Grub2, iPXE and MirOS bsd4grml boot options for 64bit ISO
- Added wallpaper
- Fixed lang boot option for grml-small flavour
As you might notice the grml-small flavour came back. So it’s two flavours (grml-full + grml-small) and two architectures (x86 + amd64) now. The grml96 option - which provides the x86 and the amd64 version on one single ISO (grml96 = grml32 + grml64) - is available for your service as well.
We want to thank all the people involved in this magnificent and awesome release. The Grml Developers, our Contributors and all the other people involved in this release.
More information is available in the release notes of Grml 2012.05. Now download the latest Grml ISO and spread the word!
First Release Candidate of Grml version 2012.05 released
We are proud to announce the first release candidate of the upcoming version 2012.05, code-named ‘Ponyhof’!
For detailed information about the changes between 2011.12 and 2012.05 have a look at the official release announcement.
Several tools that have been reported to be missing on the downsized 2011.12 release have been re-added. This release also brings the grml-small flavour back to life.
Please test the ISOs and everything you usually use and report back, so we can complete the stable release soon. If no major problems come up, the next iteration will be the stable release, which is scheduled for end of May.
New Grml developer: Evgeni Golov
We’re proud to be able to announce that Evgeni ‘Zhenech’ Golov joined the Grml team as developer. Welcome in the team, Evgeni!
Grml featured in Linux User 03/2012
The german Linux User magazine provides an article about Grml, including an interview with Grml developer Mika and the Grml 2011.12 release shipped on DVD. Grab the Linux User 03/2012 edition while it’s fresh! :)
We want you!
Recently two Grml developers sadly left our development team. Christian Hofstaedtler and Gerfried Fuchs, we wish you all the best - thanks for all your work within the Grml community!
Now you might be wondering how you could become a Grml developer. We’re happy to announce grml.github.com, a place which should get interested people ready to contribute without much headaches. Please help us making Grml an even better kick ass solution!
10 reasons why you should use Grml instead of …
With the release of Grml 2011.12 we were regularly asked what distinguishes Grml from other Live-CDs. The following items lists some reasons why you should consider using Grml instead of another Distribution for Installation&Rescue :
- handy scripts, like grml-chroot, a wrapper around chroot which will automatically bind /dev, /sys and /proc to the chroot
- the
netscriptboot option. This option will download an executable from the network and execute as root - grml-debootstrap, a tool for automated Debian installations
- grml2usb simple but powerful tools to create customized Grml images within minutes
- ZSH as default shell with a very good and comfortable zshrc
- the
netconfigboot option. This option will download an archive from the network and unpack it on top of the current root filesystem - automatically start the ssh server with the
sshboot-parameter - Boot your Grml ISO-image directly from your existing GRUB setup with loopback.cfg
- Create your own customized Grml Distribution with the same tool we release our ISO-images: grml-live
- start arbitrary services without remastering the squashfs, just specify the the
serviceboot option - EFI support, we arrived late with it but we support it now out of the box even with grml2usb
What are your reasons using Grml instead of other Live CDs? What are you missing from Grml?
Grml - new stable release 2011.12 available
I am proud to announce our Christmas Gift to the community. We just released Grml 2011.12 - Knecht Rootrecht, just in time to put it under the Christmas tree. Download the latest Grml ISO and spread the word.
There were quite a lot of changes between RC1 and the new stable release. The most important ones are:
- Update to Kernel 3.1.6
- Easier remastering with grml-live and existing Grml ISO images
- New GRUB boot theme
- SYSLINUX will indicate its boot menu with one beep
- GRUB will indicate its boot menu with three beeps
- Enable all mixer controls at startup and set volume to 75%
- Reworked and more flexible GRUB config file handling
- grml2usb - use the GRUB configuration from the ISO image instead of creating a new one
- Additional keybindings for fluxbox
- Fix keyboard layout bug
You can get Grml now in 3 options - grml32, grml64 and grml96 (32+64, featuring both Grml versions).
One flavour, two architectures, three options (grml32, grml64, and grml96).
I want to thank all the people involved in this magnificent and awesome release. The Grml Developers, our Contributors and all the other people involved in this release.
Create a Grml ISO image with your own ssh keys for password less login
In this article we will show you how you can leverage grml-autoconfig to create a Grml ISO which will automatically start an ssh server and use your own ssh keys instead of the traditional password based login. This allows Grml to be used not only for interactive rescue operations but also for remote or automated setups.
Starting with Grml 2009.05 we streamlined the support of hooking into our boot-process in grml-autoconfig thanks to the patches from Marc ‘Zugschlus’ Haber. Now it is possible to execute arbitrary scripts, unpack archives or install packages at startup not only directly from the Live CD but also from partitions. This allows you to create customized Grml Images with ease without the need to modify the squashfs image (usually known as remastering). In this example we will add the necessary files directly onto the ISO image but you can also use a USB stick instead. Please make sure you read the grml-autoconfig manpage
The first step is to create a directory which will contain all the additional files to be copied onto the ISO image. In this example we use /tmp/grml_overlay/
mkdir /tmp/grml_overlay
The next step is to create an archive containing the ssh keys. For this step you need either fakeroot or run the commands as root.
TMPDIR="/tmp/grml_config"
cd "$TMPDIR" || mkdir "$TMPDIR" && cd "$TMPDIR"
fakeroot
mkdir --parent root/.ssh home/grml/.ssh
chmod 0700 root/.ssh home/grml/.ssh
cp /home/uli/.ssh/id_rsa.pub root/.ssh/authorized_keys
cp /home/uli/.ssh/id_rsa.pub home/grml/.ssh/authorized_keys
chown -R 1000:1000 home/grml
tar --numeric-owner -j -c -f /tmp/grml_overlay/config.tbz .
This will create an archive named /tmp/grml_overlay/config.tbz containing all the files we created in our directory. Please make sure to replace the cp command with your own ssh keys. As we used fakeroot in this example you can manipulate file permissions without the need to run these commands as root.
Now we have everything what’s needed prepared and can just run grml2iso and specify the additional boot parameters as well as the overlay directory.
grml2iso -b "config ssh" -c /tmp/grml_overlay -o my-grml.iso ./grml64_2011.12.iso
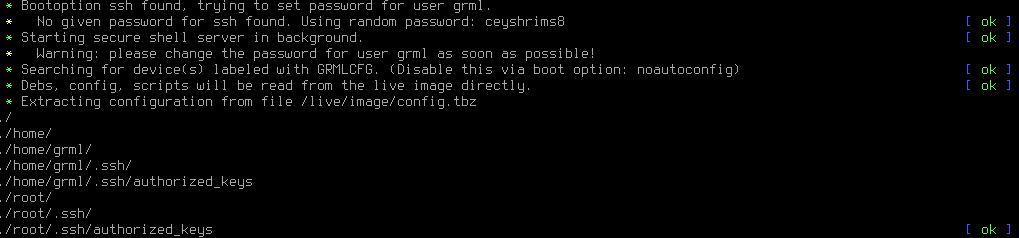 This will create a modified Grml ISO named my_grml.iso and add the bootparameters config ssh to all the existing boot-entries and copy all files from the /tmp/grml_overlay directory onto your modified ISO image. With the config parameter grml-autoconfig will automatically unpack config.tbz at bootup which contains our ssh keys. The ssh parameter will automatically start the ssh server and set a random password for the grml user. But as we deployed our ssh keys we don’t care about the password anyway. For a list of all boot parameters have a look at the Grml cheatcodes.
This will create a modified Grml ISO named my_grml.iso and add the bootparameters config ssh to all the existing boot-entries and copy all files from the /tmp/grml_overlay directory onto your modified ISO image. With the config parameter grml-autoconfig will automatically unpack config.tbz at bootup which contains our ssh keys. The ssh parameter will automatically start the ssh server and set a random password for the grml user. But as we deployed our ssh keys we don’t care about the password anyway. For a list of all boot parameters have a look at the Grml cheatcodes.
During startup of Grml you will notice some additional log messages indicating the unpacking of your created archive. This shows that everything works like intended.
Combining different boot parameters in Grml like config and ssh allows you to create customized and tailored distributions for your own needs without having to dig into the remastering process. With the availability of tools like grml2usb and grml2iso you can easily create customized tools based on Grml without the need to develop everything from scratch. We showed how you can leverage grml2iso to create a Rescue CD based on Grml with ssh keys for remote login.
Upcoming accessibility changes for Grml 2011.12
The upcoming Grml 2011.12 will have some changes in the accessibility features shipped with Grml. Until Grml 2011.12 it was possible to start brltty automatically via the bootoption brltty. The problem with this approach was that it was never clear when you had to enter the bootoptions as there was no sound to indicate boot menu. We also do not have the necessary hardware to test the releases with brltty. With that in mind and the integration of speakup in the kernel we decided to remove the additional accessibility boot-parameters for Grml 2011.12 as we never tested them anyway.
But we added some important changes to improve the accessibility. Starting with Grml 2011.12 the bootloader will either beep once (if you use the default syslinux one) or will play 3 beeps (grub) to indicate the boot menu. Afterwards you can easily change the boot parameters if you press TAB (syslinux) or e (Grub). After the bootup Grml will play some tunes to indicate the finished boot. As per default Grml starts a text based menu you will have to press enter after the beep to enter the commandline
We think with the additional sound indicators in the boot-menu as well as the default sound to indicate the finished boot-process, Grml 2011.12 will be more accessible then ever.
I would like to thank Richard Hartmann for creating the different sound indicators for the upcoming Release
Setup of the grml infrastructure: Part 1 - IPMI
Back in August 2011 the Grml Team received a new Server & Hosting furnished by Hostway. The Server is hosted in their DataCenter in Hannover. As the new Server is dedicated for the Grml Infrastructure we chose to create a new system from scratch. The new infrastructure contains many pieces like puppet, libvirt, ldap and many more. In the next few weeks we will provide some insights into our current Server Setup. So expect some interesting posts about system administration.
We start off with IPMI (Intelligent Platform Management Interface). IPMI is the interface to the BMC (Baseboard management controller), which let’s you read sensor data or just shutdown or reboot you server. IPMI may be used over lan or directly (in-band) with the help of a kernel module (ipmi_si) that implements the ipmi driver. In newer servers you may find a virtual usb to eth interface (e.g. IBM IMM in contrast to IBM RSA). First of all we need to setup a new user/admin account instead of the default one. To list all users run:
ipmitool user list 1
The digit 1 indicates channel 1.
Create user jimmy:
ipmitool user set name 2 jimmy
ipmitool user set password 2 mysecret
2 is for userid 2 which was the first free id in my case. Next we need to setup networking:
ipmitool lan set 1 ipaddr 192.168.2.6
ipmitool lan set 1 defgw ipaddr 192.168.2.1
ipmitool lan print 1
Digit 1 is again for channel 1.
Now you can test your ipmi setup over the network:
ipmitool -I lan -H 192.168.1.6 -U jimmy bmc info
You’ll be prompted for the password and receive some infos of the bmc controller.
Here are some more examples:
ipmitool -I lan -H 192.168.1.6 -U jimmy chassis power status
ipmitool -I lan -H 192.168.1.6 -U jimmy chassis power off
ipmitool sensor get "BB Ambient Temp"
ipmitool sensor get "CPU Fan"
The first one checks the power status of the server, e.g. on or off and the second one powers the server off. The last two read some sensor data. Read the man page of ipmitool to find out more ;-)
There’s a lot more about IPMI but this should help you to get started.
Remastering Grml without modifying the squashfs or create your own customized Grml CDs
In our last Blog entry about remastering Grml 2011.12 we described a method remastering Grml with grml-live, the tool used to generate the official Grml ISOs.
Often you don’t need all the power and flexibility of grml-live but just want to add or change some default boot parameters and use this as your default image. For example you may want to have an ISO image which automatically starts sshd and sets the password to a specific value or downloads an executable and run it at startup. This can easily be done with grml2iso a tool based on grml2usb which allows you to create customized iso images.
Grml will automatically start sshd and set the password for the grml user if you specify the ssh boot-parameter. This allows you to remotely control your Grml CD. To create such a CD just run:
grml2iso -b “ssh=grml-password” -o my_grml.iso ./grml64_2011.12.iso
This will create a modified Grml ISO named my_grml.iso and add the bootparameter ssh=grml-password to all the existing boot-entries.
grml2usb does not offer the same flexibility as grml-live but grml2usb/grml2iso is often good enough to help you to achieve what you want without the need to modify the squashfs file.